Connect to a TiDB Dedicated Cluster via Private Endpoint with AWS
This document describes how to connect to your TiDB Dedicated cluster via private endpoint with AWS.
TiDB Cloud supports highly secure and one-way access to the TiDB Cloud service hosted in an AWS VPC via the AWS PrivateLink, as if the service were in your own VPC. A private endpoint is exposed in your VPC and you can create a connection to the TiDB Cloud service via the endpoint with permission.
Powered by AWS PrivateLink, the endpoint connection is secure and private, and does not expose your data to the public internet. In addition, the endpoint connection supports CIDR overlap and is easier for network management.
The architecture of the private endpoint is as follows:
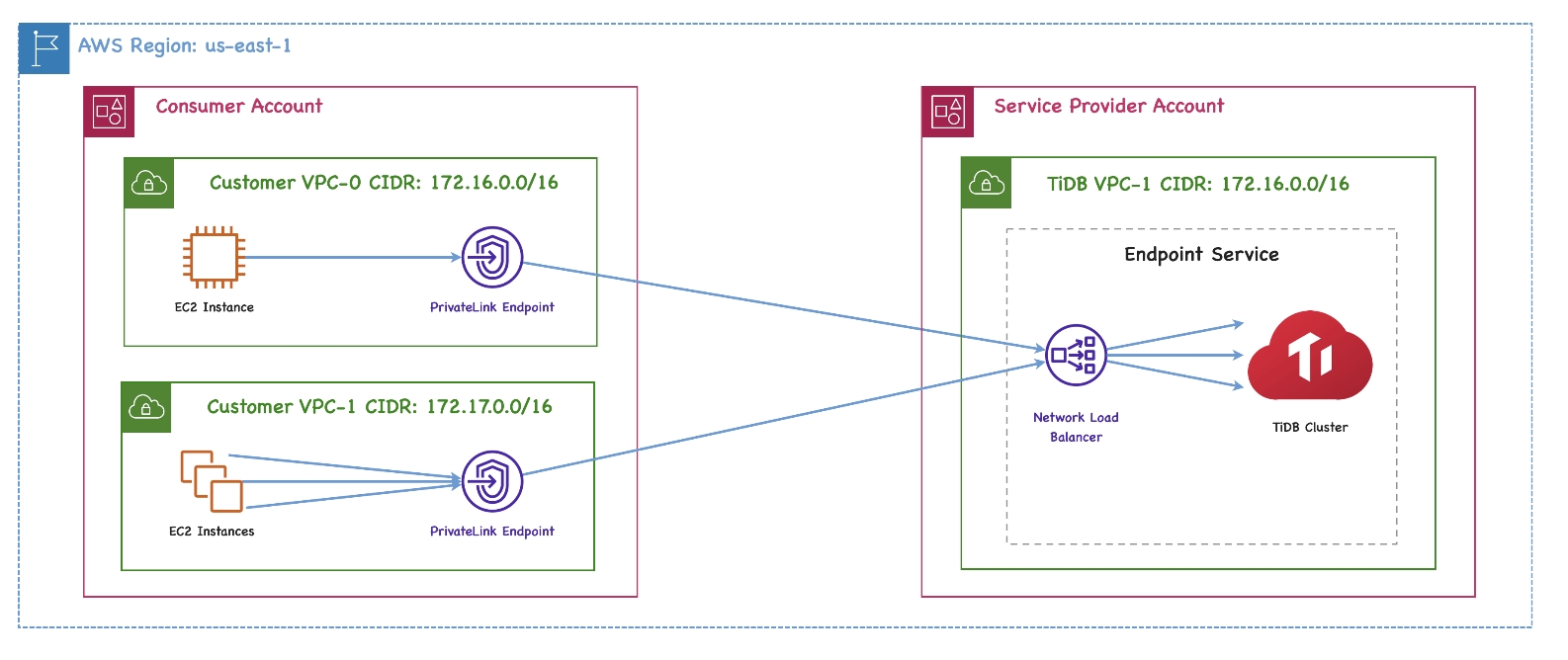
For more detailed definitions of the private endpoint and endpoint service, see the following AWS documents:
Restrictions
- Only the
Organization Ownerand theProject Ownerroles can create private endpoints. - The private endpoint and the TiDB cluster to be connected must be located in the same region.
In most scenarios, you are recommended to use private endpoint connection over VPC peering. However, in the following scenarios, you should use VPC peering instead of private endpoint connection:
- You are using a TiCDC cluster to replicate data from a source TiDB cluster to a target TiDB cluster across regions, to get high availability. Currently, private endpoint does not support cross-region connection.
- You are using a TiCDC cluster to replicate data to a downstream cluster (such as Amazon Aurora, MySQL, and Kafka) but you cannot maintain the endpoint service on your own.
- You are connecting to PD or TiKV nodes directly.
Set up a private endpoint with AWS
To connect to your TiDB Dedicated cluster via a private endpoint, complete the prerequisites and follow these steps:
- Choose a TiDB cluster
- Check the service endpoint region
- Create an AWS interface endpoint
- Accept the endpoint connection
- Enable private DNS
- Connect to your TiDB cluster
If you have multiple clusters, you need to repeat these steps for each cluster that you want to connect to using AWS PrivateLink.
Prerequisites
- Log in to the TiDB Cloud console.
- Click in the lower-left corner, switch to the target project if you have multiple projects, and then click Project Settings.
- On the Project Settings page of your project, click Network Access in the left navigation pane, and click the Private Endpoint tab.
- Click Create Private Endpoint in the upper-right corner, and then select AWS Private Endpoint.
Step 1. Choose a TiDB cluster
- Click the drop-down list and choose an available TiDB Dedicated cluster.
- Click Next.
Step 2. Check the service endpoint region
Your service endpoint region is selected by default. Have a quick check and click Next.
Step 3. Create an AWS interface endpoint
If you see the Endpoint Service Ready message, take note of your endpoint service name from the command in the lower area of the console for later use. Otherwise, wait 3 to 4 minutes to let TiDB Cloud create an endpoint service for your cluster.
aws ec2 create-vpc-endpoint --vpc-id ${your_vpc_id} --region ${your_region} --service-name ${your_endpoint_service_name} --vpc-endpoint-type Interface --subnet-ids ${your_application_subnet_ids}
Then create an AWS interface endpoint either using the AWS Management Console or using the AWS CLI.
- Use AWS Console
- Use AWS CLI
To use the AWS Management Console to create a VPC interface endpoint, perform the following steps:
Sign in to the AWS Management Console and open the Amazon VPC console at https://console.aws.amazon.com/vpc/.
Click Endpoints in the navigation pane, and then click Create Endpoint in the upper-right corner.
The Create endpoint page is displayed.
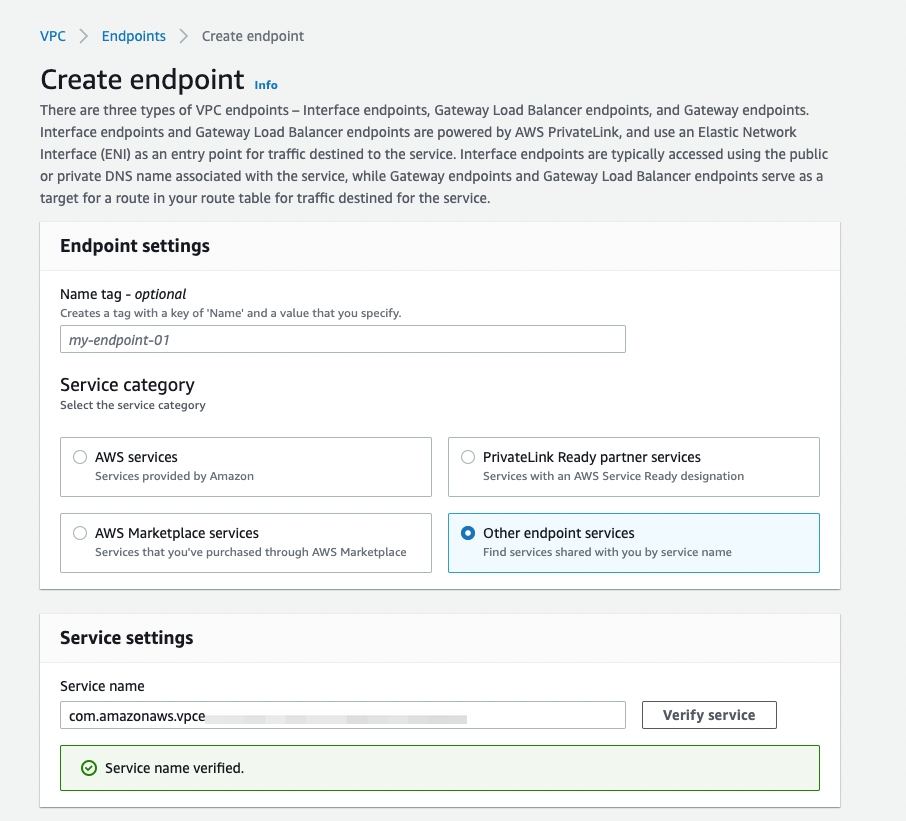
Select Other endpoint services.
Enter the service name that you found in the TiDB Cloud console.
Click Verify service.
Select your VPC in the drop-down list.
Select the availability zones where your TiDB cluster is located in the Subnets area.
Select your security group properly in the Security groups area.
Click Create endpoint.
To use the AWS CLI to create a VPC interface endpoint, perform the following steps:
- Fill in the VPC ID and Subnet IDs fields on the private endpoint creation page. You can get the IDs from your AWS Management Console.
- Copy the command in the lower area of the page and run it in your terminal. Then click Next.
Step 4. Accept the endpoint connection
- Go back to the TiDB Cloud console.
- Fill in the box with your VPC endpoint ID on the Create Private Endpoint page.
- Click Next.
Step 5. Enable private DNS
Enable private DNS in AWS. You can either use the AWS Management Console or the AWS CLI.
- Use AWS Console
- Use AWS CLI
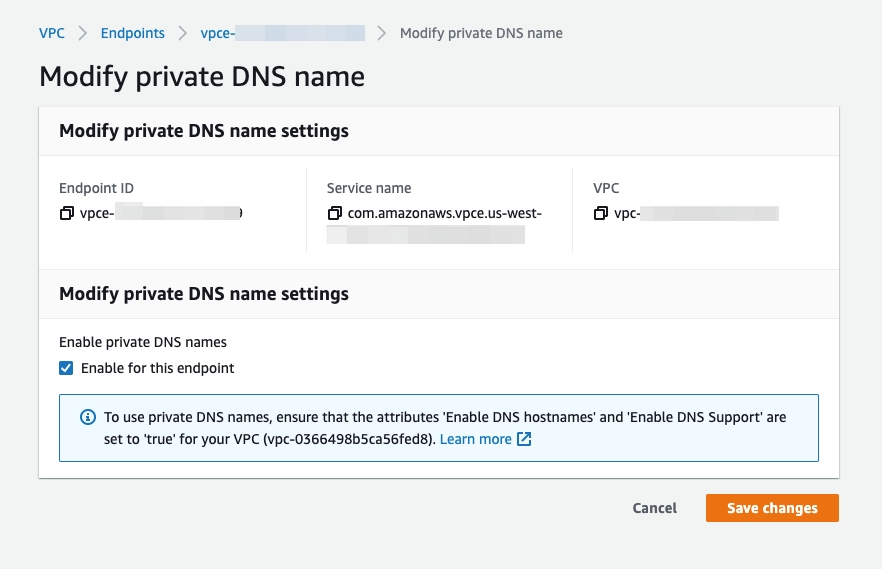
To enable private DNS in your AWS Management Console:
Go to VPC > Endpoints.
Right-click your endpoint ID and select Modify private DNS name.
Select the Enable for this endpoint check box.
Click Save changes.
To enable private DNS using your AWS CLI, copy the command and run it in your AWS CLI.
aws ec2 modify-vpc-endpoint --vpc-endpoint-id ${your_vpc_endpoint_id} --private-dns-enabled
Click Create in the TiDB Cloud console to finalize the creation of the private endpoint.
Then you can connect to the endpoint service.
Step 6. Connect to your TiDB cluster
After you have enabled the private DNS, go back to the TiDB Cloud console and take the following steps:
- On the Clusters page, click ... in the Action column.
- Click Connect. A connection dialog is displayed.
- Select the Private Endpoint tab. The private endpoint you just created is displayed under Step 1: Create Private Endpoint.
- Under Step 2: Connect your connection, click Connect, click the tab of your preferred connection method, and then connect to your cluster with the connection string. The placeholders
<cluster_endpoint_name>:<port>in the connection string are automatically replaced with the real values.
Private endpoint status reference
When you use private endpoint connections, the statuses of private endpoints or private endpoint services are displayed on the Private Endpoint page.
The possible statuses of a private endpoint are explained as follows:
- Not Configured: The endpoint service is created but the private endpoint is not created yet.
- Pending: Waiting for processing.
- Active: Your private endpoint is ready to use. You cannot edit the private endpoint of this status.
- Deleting: The private endpoint is being deleted.
- Failed: The private endpoint creation fails. You can click Edit of that row to retry the creation.
The possible statuses of a private endpoint service are explained as follows:
- Creating: The endpoint service is being created, which takes 3 to 5 minutes.
- Active: The endpoint service is created, no matter whether the private endpoint is created or not.
- Deleting: The endpoint service or the cluster is being deleted, which takes 3 to 5 minutes.
Troubleshooting
I cannot connect to a TiDB cluster via a private endpoint after enabling private DNS. Why?
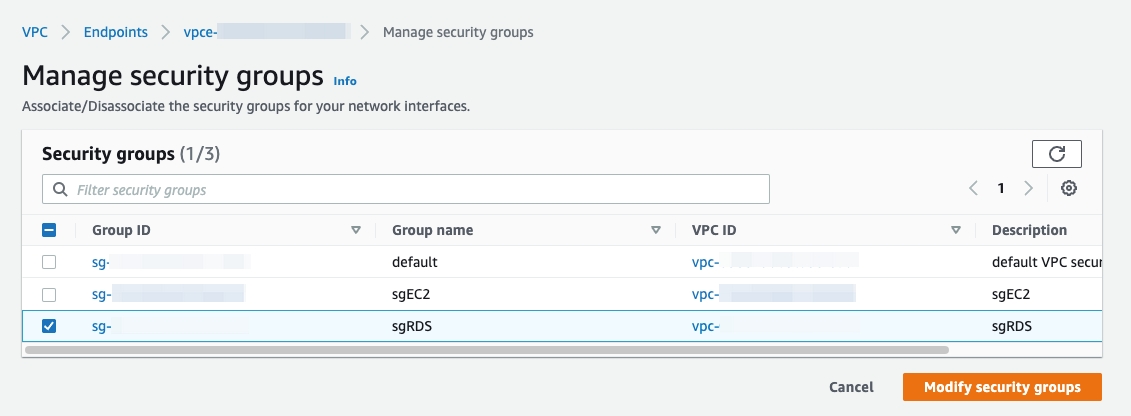
You might need to properly set the security group for your VPC endpoint in the AWS Management Console. Go to VPC > Endpoints. Right-click your VPC endpoint and select the proper Manage security groups. A proper security group within your VPC that allows inbound access from your EC2 instances on Port 4000 or a customer-defined port.
I cannot enable private DNS. An error is reported indicating that the enableDnsSupport and enableDnsHostnames VPC attributes are not enabled
Make sure that DNS hostname and DNS resolution are both enabled in your VPC setting. They are disabled by default when you create a VPC in the AWS Management Console.